FREE Microsoft Azure Architect Design Questions and Answers
Your business offers customer support for various Azure subscriptions as well as outside hosting companies.
You are creating a system for central monitoring. The following needs to be addressed by the solution:
‥ Collect log and diagnostic data from all the third-party hosting providers into a centralized repository.
‥ Collect log and diagnostic data from all the subscriptions into a centralized repository.
‥ Automatically analyze log data and detect threats.
‥ Provide automatic responses to known events.
What Azure service ought to be incorporated into the solution?
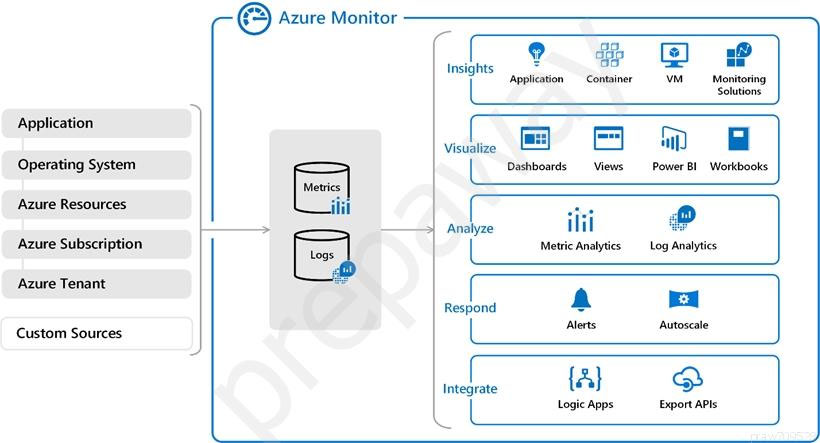
The figure that follows provides a high-level overview of Azure Monitor. The two primary forms of data that Azure Monitor uses are metrics and logs, and these data storage are located in the middle of the figure. The sources of monitoring data that fill these data repositories are shown on the left. The various tasks that Azure Monitor carries out with this data are shown on the right. Analyzing, alerting, and broadcasting to external systems are some examples of this.
You are creating an Azure resource deployment using templates from Azure Resource Manager. Secrets will be kept in Azure Key Vault during deployment.
You must suggest a solution that satisfies the following criteria:
‥ Prevent the IT personnel handling the deployment from immediately obtaining the secrets from Key Vault.
‥ Apply the least privilege principle.
Which two steps would you suggest? Each right response offers a piece of the answer.
Please select 2 correct answers
‥ Set enabledForTemplateDeployment on the key vault to true in order to gain access to it during template deployment.
‥ The Microsoft.KeyVault/vaults/deploy/action permission for the scope of the resource group and key vault is required for the person who installs the template.
You have three Azure regions' worth of web apps in your Azure subscription.
The following requirements must be fulfilled by the implementation of Azure Key Vault:
‥ All keys must be readable in the case of a local outage.
‥ Key Vault access is required for any subscription-based web apps.
‥ The least amount of Key Vault resources need to be deployed and managed.
How many Key Vault instances should you set up?
Your key vault's contents are duplicated both locally and to a second region that is at least 150 miles away but still part of the same geographic area. This keeps the strength of your keys and secrets. For information on certain area pairs, see the Azure paired regions document.
For instance, your application must exchange some information with both Europe West and Europe North. Try to keep these to a minimum. Put these in one of the two regions' key vaults. Using the same URI in both places. Internally, Microsoft will fail over the Key Vault service.
Your Azure Active Directory (Azure AD) tenancy already exists.
Using Azure Storage, you want to give users access to shared files. Depending on their user account or group membership, the users will receive varying degrees of access to various Azure file shares.
Which additional Azure services should be leveraged to support the proposed rollout must be suggested.
What should the recommendation contain?
Two different types of Domain Services are supported by Azure Files for identity-based authentication through Server Message Block (SMB): on-premises Active Directory Domain
Azure Active Directory Domain Services (Azure AD DS) and Active Directory Domain Services (AD DS).
You want to set up five Azure virtual machines for the App1 application, which will be deployed. To run App1, more virtual machines will be introduced later.
You must suggest a method to satisfy each of the conditions for the virtual machines that will run App1:
‥ Check that the virtual machines can access an Azure key vault, instances of Azure Logic Apps, and an Azure SQL database by authenticating to Azure Active Directory (Azure AD).
‥ When you deploy more virtual machines, avoid giving them new roles and permissions for Azure services.
‥ Prevent keeping certificates and secrets on the virtual machines.
‥ Reduce the administrative work required to manage identities.
Which identification type ought to be mentioned in the recommendation?
One function of Azure Active Directory is managed identities for Azure resources.
Shared managed identities can be assigned by users. An Azure resource can be linked to more than one user-assigned managed identity.
You are creating an architecture for a set of microservices that will run on an Azure Kubernetes Service (AKS) cluster, be consumed by apps running on Azure virtual machines, and share a virtual network with the AKS cluster.
You must create a solution that complies with the following criteria in order to expose the microservices to the consumer apps:
‥ Mutual TLS authentication must be used to safeguard ingress access to the microservices, which must be limited to a single private IP address.
‥ Incoming microservice calls must be rate-limited in terms of quantity.
‥ Costs must be kept to a minimum.
What should the solution contain?
Deploying APIM (API Management) inside the cluster VNet is one option.
There is no need to expose the AKS cluster to the public because all API traffic will stay inside the VNet and the apps that use the microservices may be within the same VNet. You can introduce API Management into the cluster VNet for these cases. Supports for API Management Premium tier
deployment of a VNet.
You have a tenant called contoso.com in Azure Active Directory (Azure AD). Group1 is one of the tenants' groups. All of the administrative user accounts are in Group1.
You find many attempts to enter into the Azure portal coming from nations where administrative users are NOT employed.
You must make sure that Azure Multi-Factor Authentication (MFA) is required for all attempts to enter into the Azure portal from certain nations.
Solution: Construct a Group1 Access Review.
Is the goal achieved by this solution?
Use Azure AD Privileged Identity Management instead.
A service called Azure Active Directory (Azure AD) Privileged Identity Management (PIM) allows you to manage, restrict, and keep an eye on who has access to key resources within your company.